WooCommerce: How Secure Is IT? [ANALYSIS]

As part of a comprehensive analysis of the key points of WordPress and WooCommerce, we could not bypass the WooCommerce security issues.
When looking at the core of the platform, there are generally no striking security issues in WordPress. There are only relatively narrow places that can potentially cause hacking. The vast majority of these bottlenecks in WordPress sites are actually easy to control. The core of this system has gone a long way to development, so it’s quite safe. Surprising as it may sound, web developers are serious about security and release patches very quickly. One of the strengths of WordPress is the ease of upgrading and the high speed of the development cycle.
A large part of potential security issues emerge due to end users’ short-sightedness in choosing themes and plugins with dangerous codes and using poor quality hosting.
Let’s start with some statistics
One of the articles on WP White Security gives the statistics of hacked websites:
- 41% were hacked through a vulnerability of the hosting account
- 29% were hacked via a security issue in the WordPress theme they were using
- 22% were hacked via a security issue in the WordPress plugins they were using
- 8% were hacked because of a weak password
Below is a chart of the types of vulnerabilities that are used for hacking WordPress sites.
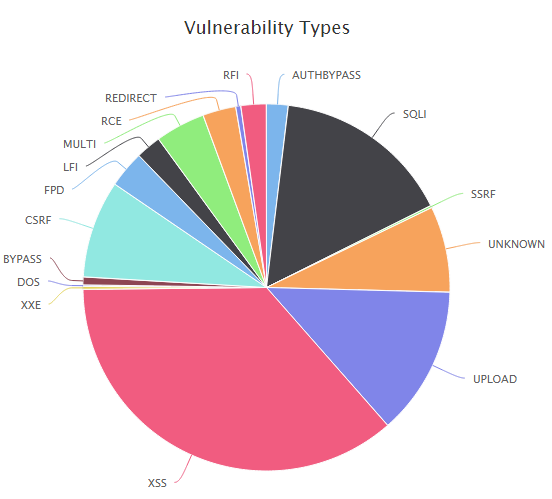
As you can see, the WordPress core is very rarely the cause of hacking, and most of the vulnerabilities given in the chart appear due to the bottlenecks of third-party plugins.
One of our objectives in developing a comprehensive WooCommerce solution is to research in more detail all possible security vulnerabilities and provide maximum security for online retailers. We will cover our research in greater detail in our next articles.
Below are listed the most common security recommendations that can be currently found on the Internet.
Recommendations for improving WordPress and WooCommerce security
Update WordPress
Each new version of WordPress contains changes that may include patches for security bottlenecks found in earlier versions. The old versions of the platforms that have not been updated for a long time are often exposed to hacking.
Choose reliable hosting
41% of the hacks were enabled due to security issues on hosting platforms, so choosing a high-quality hosting company is very important. A good hosting platform should meet the following criteria:
- Support for the latest versions of PHP and MySQL
- Optimized for WordPress
- Scanning for malware and junk files
Also, do not forget to backup the database and files.
Important installation settings
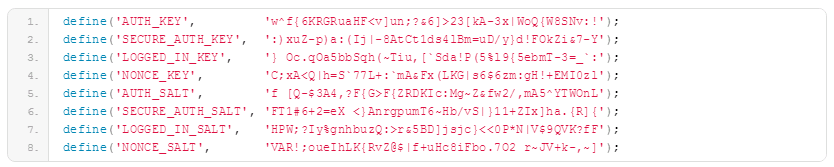
WordPress Security Keys. Keys improve the encryption of information stored in visitor cookies. They also make it harder for your password to be hacked, since random elements are added to it. Keys can be changed in wp-config.php:
Changing prefixes to database tables. This can help prevent SQL injection vulnerabilities. You will find the prefix to the table names in your wp-config.php file:
$table_prefix = ‘wp_’;
WordPress Themes and Plugins
Through the holes in the security of plugin codes and themes, malicious users get access to sites in more than 50% of cases. Therefore, it is important to weigh all pros and cons before using this or that plugin/theme.
Use the correct file/directory permissions
This is another important step in improving security. Installing 777 directory permissions (everyone can read, write and execute) allows attackers to download various files to this directory or modify already existing ones. It is recommended to set the following permissions (usually you can do this through the hosting panel or the FTP client):
- All directories must have 755 or 750 permissions
- All files must have 644 or 600 permissions
- For wp-config.php, set 600 permissions.
Disable script error messages
If any of your plugins or themes contains an error, a message about it may appear on the site. It usually shows the complete path to your website directory. This information is useful for hackers. You can disable script error messages by adding the following lines to the wp-config.php file:
error_reporting(0);
@ini_set(‘display_errors’, 0);
Protecting through the .htaccess file
Disclaimer! This recommendation is a common practice, but we have not tested it yet. We will check it out and describe the results in our next articles. Use it at your discretion. We will be very grateful if you share your thoughts on it with us in the comments below or through contacts on our website.
Please note that the following codes should be placed in a file out of #BEGIN WordPress and # END WordPress tags, since all that lies between these tags is changing WordPress.
The wp-config.php file is very important, and it can be protected from external access by adding the following lines to .htaccess:
<files wp-config.php>
order allow,deny
deny from all
</files>
/wp-includes/ directory contains many crucial files from the WordPress distribution. WordPress simply will not work without them. To protect this directory you can add the following lines in .htaccess file at the root of the site:
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]
RewriteRule !^wp-includes/ – [S=3]
RewriteRule ^wp-includes/[^/]+.php$ – [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+.php – [F,L]
RewriteRule ^wp-includes/theme-compat/ – [F,L]
or you can use the following rule that redirects any direct requests from PHP files to a chosen page (in the following example the server will generate 404 page and status code).
# Restrict access to PHP files from plugin and theme directories
RewriteCond %{REQUEST_URI} !^/wp-content/plugins/file/to/exclude\.php
RewriteCond %{REQUEST_URI} !^/wp-content/plugins/directory/to/exclude/
RewriteRule wp-content/plugins/(.*\.php)$ – [R=404,L]
RewriteCond %{REQUEST_URI} !^/wp-content/themes/file/to/exclude\.php
RewriteCond %{REQUEST_URI} !^/wp-content/themes/directory/to/exclude/
RewriteRule wp-content/themes/(.*\.php)$ – [R=404,L]
You can also block people from viewing the contents of the directories on the site through the browser. To do this, add the following code in the .htaccess file:
Options All -Indexes
To protect the .htaccess file you should write the following in it:
<Files .htaccess>
order allow,deny
deny from all
</Files>
Protect Debug Logs
When developing plugins and themes or installing WordPress, developers or system administrators can enable debug logs that will record all PHP errors.
WordPress uses the WP_DEBUG constant defined in wp-config.php. The constant is used to start the debugging mode in WordPress. By default, the constant is set as false.
Developers and system administrators can also include WP_DEBUG_LOG and WP_DEBUG_DISPLAY comparator constants in WP_DEBUG. WP_DEBUG_LOG creates a log file in the wp-contents folder, and WP_DEBUG_DISPLAY controls whether debugging is displayed in HTML pages or not.
Any of the above will be useful in developing a theme, plugin or site. However, if allowed on a finished website, this could lead to disclosure and allow attackers to view errors and additional information about the registration. You must remove the WP_DEBUG constant from the wp-config.php file, or set it as false, as shown below:
define (‘WP_DEBUG’, false);
Forcing SSL
If you want the information you transmit to be protected, you need to use an SSL protocol that ensures the integrity and confidentiality of data exchanges. In WordPress, it’s as easy as pie.
First of all, find out if your provider can use SSL. If so, then open the wp-config.php file and add the following line:
define (‘FORCE_SSL_ADMIN’, true);
Remove Readme and other unwanted files
The readme.html file is located in the root directory of WordPress; many plugins and themes also have similar files. A right solution will be to remove them, since they can be used for fingerprinting or snooping, and often contain information about the version. Clear the folders on your site from these and any other unwanted files, including install.php and wp-config-sample.php files.
Brute Force Protection Recommendations
As we develop our product, we will additionally research authorization protection issues. The most important recommendation is to use strong passwords that can not be hacked.
According to the Wikipedia table, to figure out a password of 8 characters that contains numbers and letters, you need to spend 9 months, making 100K attempts per second.
https://en.wikipedia.org/wiki/Brute-force_attack
Although you can still use the following methods.
Limit the number of authorization attempts
Hackers use brute force attacks to hack passwords, each time trying to authorize with a new password. One of the best ways to protect a site from such attacks is to install Login LockDown or Login Security Solution plugin. These plugins limit the number of website authorization attempts.
Authorization in two stages
This method makes it much more difficult to access through a brute force attack or even prevents it. The point is to use an additional code for a successful authorization. For example, this code can be sent to your mobile.
Additional recommendations for enhanced protection
The following recommendations are widespread, but we have not tested them yet. We will check them out and report in more detail in our next articles. Use them at your discretion.
We will be very grateful if you share with us your thoughts about these or other protection tips in the comments below or through contacts.
Preventing third-party PHP files running
WordPress download directory is available for writing, as WordPress sites allow their users to download new content. That’s why your wp-content/uploads directory should be considered as a potential target for hacking.
The biggest potential threat is the PHP files downloading. WordPress will not allow users to download PHP files in their administrative console; however, it may happen that a plugin or theme allows to download files without using the designated WordPress APIs. This can lead to the downloading of a malicious PHP file and, consequently, its execution on the server.
The best way to eliminating this potential security risk is to refuse the web server to execute any PHP files in the wp-content/uploads directory using the following rule:
<Directory “/var/www/content/uploads/”>
<Files “*.php”>
Order Deny,Allow
Deny from All
</Files>
</Directory>
XML-RPC Deactivation
Starting with WordPRess 3.5 version, XML-RPC is activated by default. This feature allows you to remotely connect through a variety of blog-clients to your site. It is also used for trackbacks and pingbacks. Unfortunately, malicious users often use this opportunity to attack sites.
To disable this feature, you can use Disable XML-RPC Pingback plugin, reducing the risk of your site being attacked.
Protect WordPress from XSS injections
Programmers always try to protect GET and POST requests; however, sometimes this is not enough. It is necessary to protect the blog from XSS injections and attempts to modify GLOBALS and _REQUEST variables.
The following code blocks the use of XSS injections and attempts to modify GLOBALS and _REQUEST variables. Paste the code into your .htaccess file at the root of the site.
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]
Hide the WordPress version
WordPress automatically inserts its version number into the source code of the pages. Unfortunately, it is not always possible to update the engine in time. This means that knowing what version of WordPress you have with all its drawbacks and weaknesses, the attacker may cause a lot of trouble for you. In order to hide the version of WordPress, open functions.php, which lies in the folder with the active theme of your blog (wp-content / themes / title-your-themes /) and add the following code there:
remove_action (‘wp_head’, ‘wp_generator’);
or
// remove version info from head and feeds
function complete_version_removal() {
return ”;
}
add_filter(‘the_generator’, ‘complete_version_removal’);
Write a plugin to protect against malicious URL requests
Hackers often try to find weak spots by all sorts of malicious requests. WordPress is well protected, but having extra protection will never hurt.
Create a new file named blockbadqueries.php and place it in the wp-content / plugins folder. Then just activate it through the admin panel as any other plugin.
<?php
/*
Plugin Name: Block Bad Queries
Plugin URI: perishablepress.com/press/2009/12/22/protect-wordpress-against-malicious-url-requests
Description: Protect WordPress Against Malicious URL Requests
Author URI: perishablepress.com
Author: Perishable Press
Version: 1.0
*/
global $user_ID;
if($user_ID) {
if(!current_user_can(‘level_10’)) {
if (strlen($_SERVER[‘REQUEST_URI’]) > 255 ||
strpos($_SERVER[‘REQUEST_URI’], “eval(“) ||
strpos($_SERVER[‘REQUEST_URI’], “CONCAT”) ||
strpos($_SERVER[‘REQUEST_URI’], “UNION+SELECT”) ||
strpos($_SERVER[‘REQUEST_URI’], “base64”)) {
@header(“HTTP/1.1 414 Request-URI Too Long”);
@header(“Status: 414 Request-URI Too Long”);
@header(“Connection: Close”);
@exit;
}
}
}
?>
How does it work? It’s pretty simple. This plugin checks all long requests (over 255 characters) and the eval or base64 php functions availability in URI. If this is the case, the user’s browser generates the 414 error page.
Plugins to enhance WordPress and WooCommerce security
There is a plenty of security plugins available on the Internet. Their main features are usually the protection against brute force attacks, as well as various firewalls that monitor the code and the attempts to access the admin panel.
The main security issues can be fixed by the above recommendations, along with reliable hosting. However, if you want to use firewall and monitoring, it would be helpful to pay attention to the following plugins.
Wordfence
When it comes to WordPress and WooCommerce security plugins, Wordfence is always the first one to mention. The plugin has scored 4.9 stars out of 5. When choosing security plugin, Wordfence with such an impressive result deserves your attention. It gained such a popularity thanks to many useful features:

- Extended security check
- Blocking users by IP
- Secure system login
- IPv6 compatibility
- Full support for WooCommerce sites
- Malicious code search
- Vulnerability assessment
- FireWall
- Single admin control panel for multiple blogs
All In One WP Security & Firewall
This is an easy to use, robust and reliable WordPress security plugin. It reduces security risk by verifying vulnerability, eliminating it and implementing the latest recommended practices and methods of protecting WordPress. The plugin is 100% free.

Main plugin features:
- Security of user accounts
- User authentication security
- User registration security
- Database security
- File system security
- Backup and restoring of HTACCESS and WP-CONFIG.PHP files
- Black list of users
- FireWall
- Preventing brute force attacks
- Scanning files for changes
- Spam protection in comments
- Additional features
SUCURI Security
SUCURI is another service with a good reputation in providing site protection. SUCURI’s WordPress and WooCommerce security plugin works well with file integrity monitoring, security enhancements, activity auditing, malware scanning, and many more.
- Protection against DDoS attacks
- Vulnerability assessment
- Speed optimization
- Protection from brute force attacks
- Security alert
- Recovery after hacking
- Search for malicious code
Conclusion
WordPress is the world’s most popular CMS, used by hundreds of millions of websites. Due to the wide user base, it is a potential target for hackers.
It is important to note that most hacking is done by robots, and the websites get massively hacked mainly for sending spam or the spread of viruses. The above-mentioned recommendations will protect you from 99% of automatic hacking.
One of the main tasks of our company is to continue the monitoring and testing of the bottlenecks of the plugins and themes mentioned in this article and giving advice on safety. All of our research will be posted on the relevant section of our blog.
Another articles from our comprehensive analysis of the key points of WordPress and WooCommerce:
WordPress Development Environment and Developers’ Best Practices Review
Review and Analysis of Top 10 Premium WooCommerce Themes 2017
Complete WooCommerce SEO Guide and Tips
Comments
Ready to Get Started?
Join over 100,000 smart shop owners who use Premmerce plugins to power their WooCommerce stores.
Get started